This white paper explores how CrateDB provides a scalable platform to build Generative AI applications that c…
Data teams are facing more challenges than ever. As applications generate and consume unprecedented volumes o…
At EliteOps, we are a team of engineers dedicated to delivering expert-driven cybersecurity and observability…
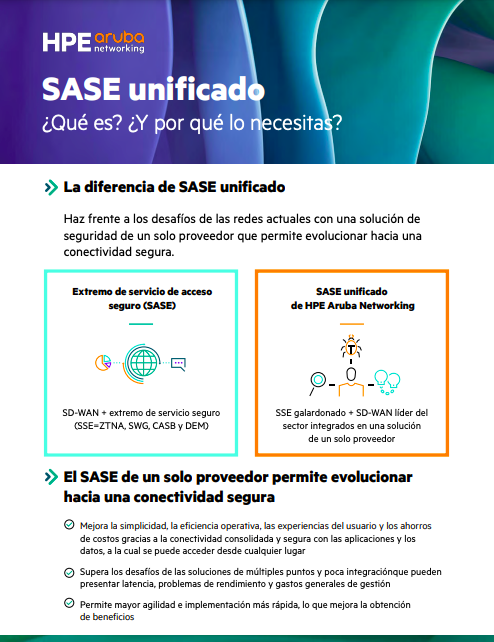
EliteOps transforms how businesses deploy and benefit from Secure Access Service Edge (SASE) solutions like Z…
Let’s discuss a topic crucial yet often overlooked. Business continuity and service availability. Imagine hav…
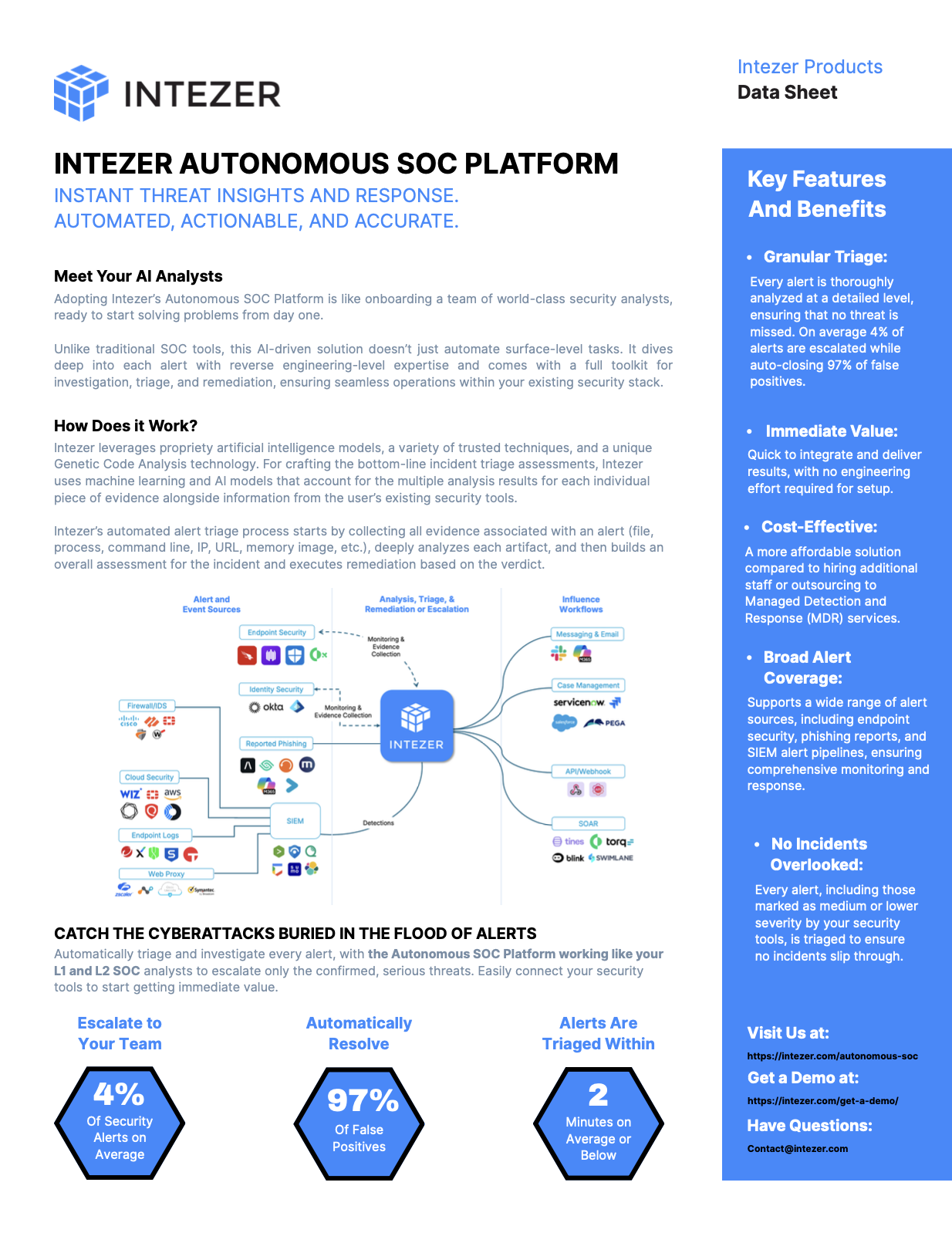
Adopting Intezer’s Autonomous SOC Platform is like onboarding a team of world-class security analysts, ready …
Every network is unique. Whether you manage data centers, cloud environments, or a hybrid of the two, seamles…
Here are some testimonials of some Intezer customers.
In 2024, digital identities became the top target for cybercriminals, serving as the convergence point for pe…
As the digital landscape continues to evolve, the rapid proliferation of cloud infrastructure and services of…
Cloud architecture serves as critical infrastructure to most modern businesses, from fully online, digital-na…
Since the early 2000s, cybersecurity and IT teams have continued to rely on standalone SIEMs to collect, aggr…
In 2015, a publicly-traded insurance company purchased a SIEM solution, which we’ll refer to as SIEM15. Three…
In today’s ever-changing landscape, nonprofits face a myriad of challenges, from shifting donation trends to …
Artificial Intelligence (AI) is transforming the way nonprofits operate, helping them to achieve their missio…
In today’s fast-paced digital landscape, executives face an increasing need to streamline operations, manage …
Most Zero Trust Network Access solutions route your traffic through a cloud broker and are good enough to secur…
Undoubtedly, CISOs have been thrust into strategic business leadership, entrusted with safeguarding intricate…
Key strategies for security, IT and engineering leaders
This e-book is designed to help readers looking for ways to get value from implementing artificial intelligen…
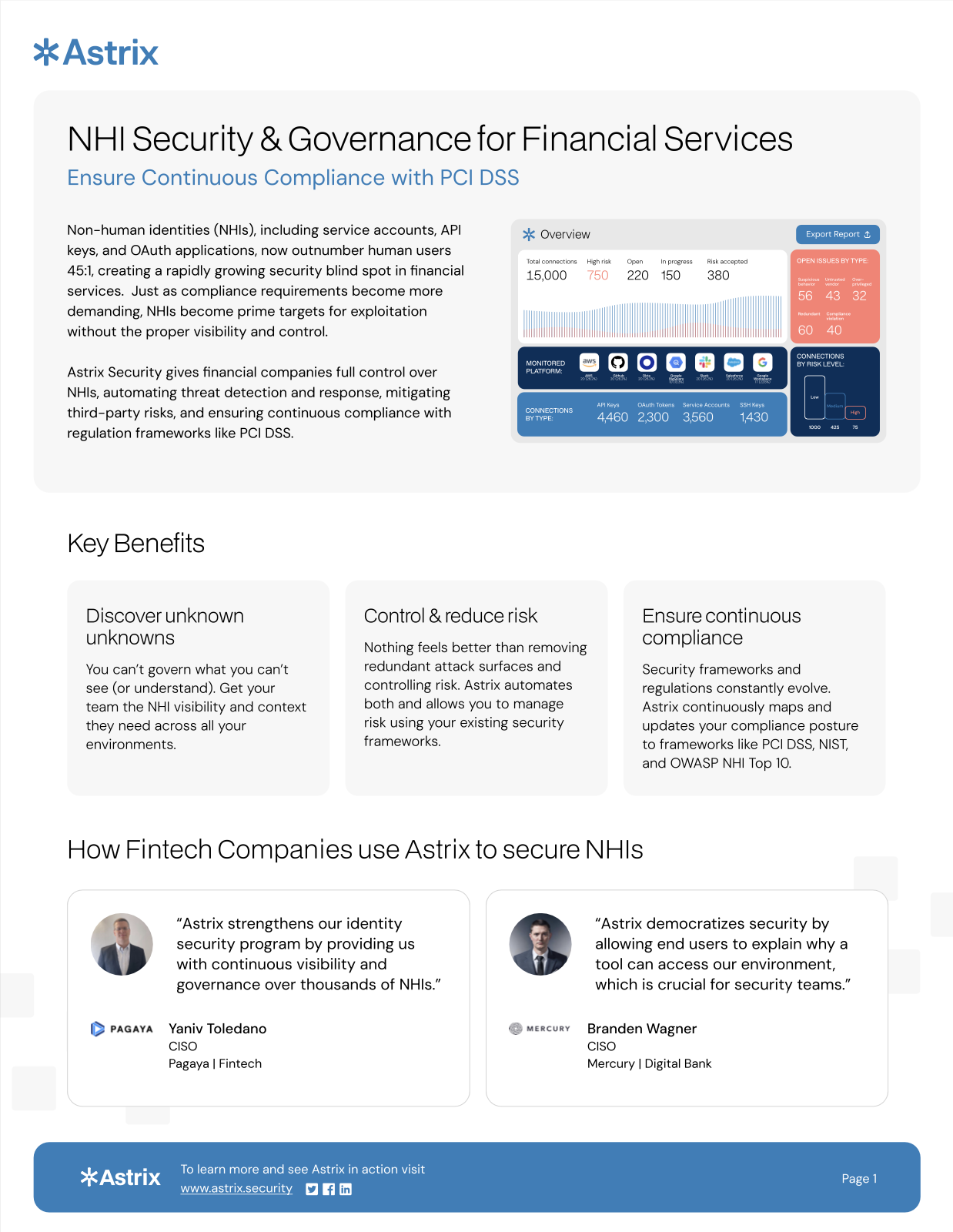
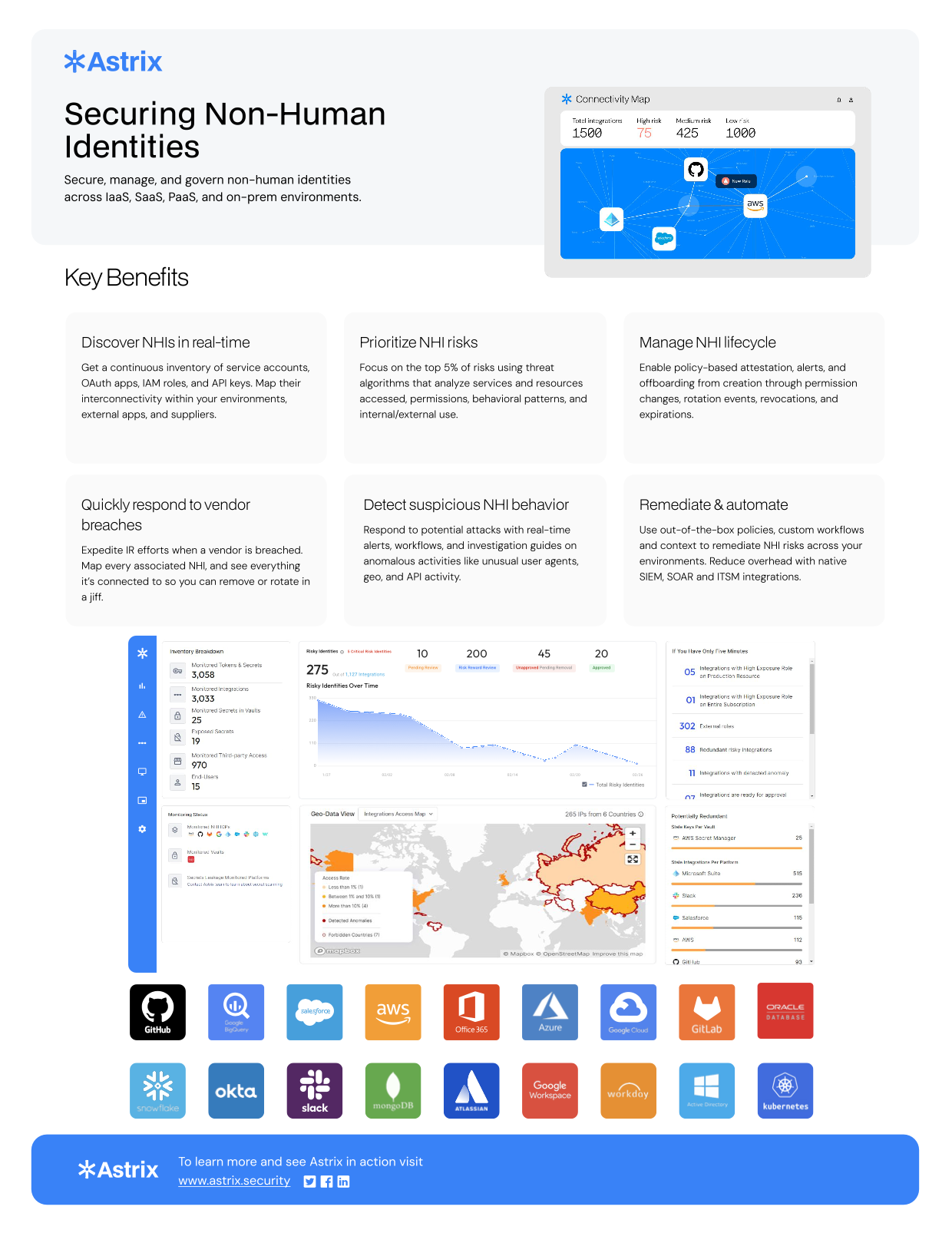
Non-human identities (NHIs), including service accounts, API keys, and OAuth applications, now outnumber huma…
Secure, manage, and govern non-human identities across laaS, SaaS, and on-prem environments.
How AI will usher in a new era of security and observability.
Today’s businesses handle vast amounts of sensitive information, such as personally identifiable information …
With the rapid expansion of digital operations, protecting sensitive data has become a top priority for organ…
The cost of an insider threat is the highest it’s ever been, as the number of insider incidents continues to …
DTEX Insider Intelligence and Investigations (DTEX i3) is an investigations and research division focused on …
This global leader in insurance and risk management has a worldwide presence with 13,000+ employees and bring…
Gurucul provides a radically clear view of cyber risk through a dynamic security analytics platform purpose-b…
Inventory health is a high-level assessment of retail's overall inventory efficiency within a specific frame …
Over the past several years, organizations have been expanding their multi-edge networking strategies to enab…
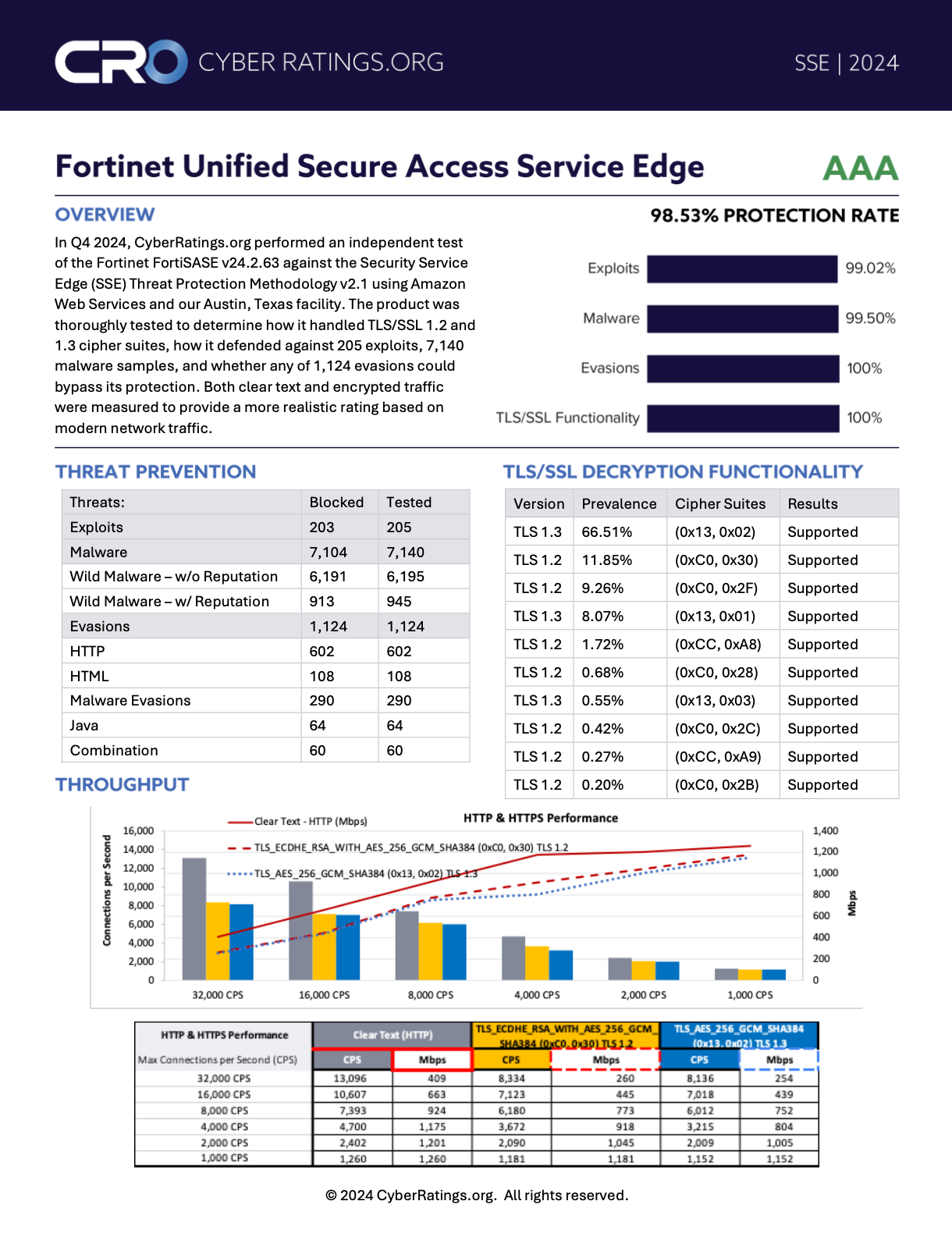
In Q4 2024, CyberRatings.org performed an independent test of the Fortinet FortiSASE v24.2.63 against the Sec…
While software-defined wide area networks (SD-WANs) offer major performance and convenience advantages over t…
New risks surface, algorithms evolve, and with. emergence of quantum computers, IT and security teams must be…
Ready or not, the race to quantum-safe readiness is on. No, there’s no doomsday clock winding down to zero an…
Astrix's NHI Security Platform is recognized by Gartner and White House as a leading solution for addressing …
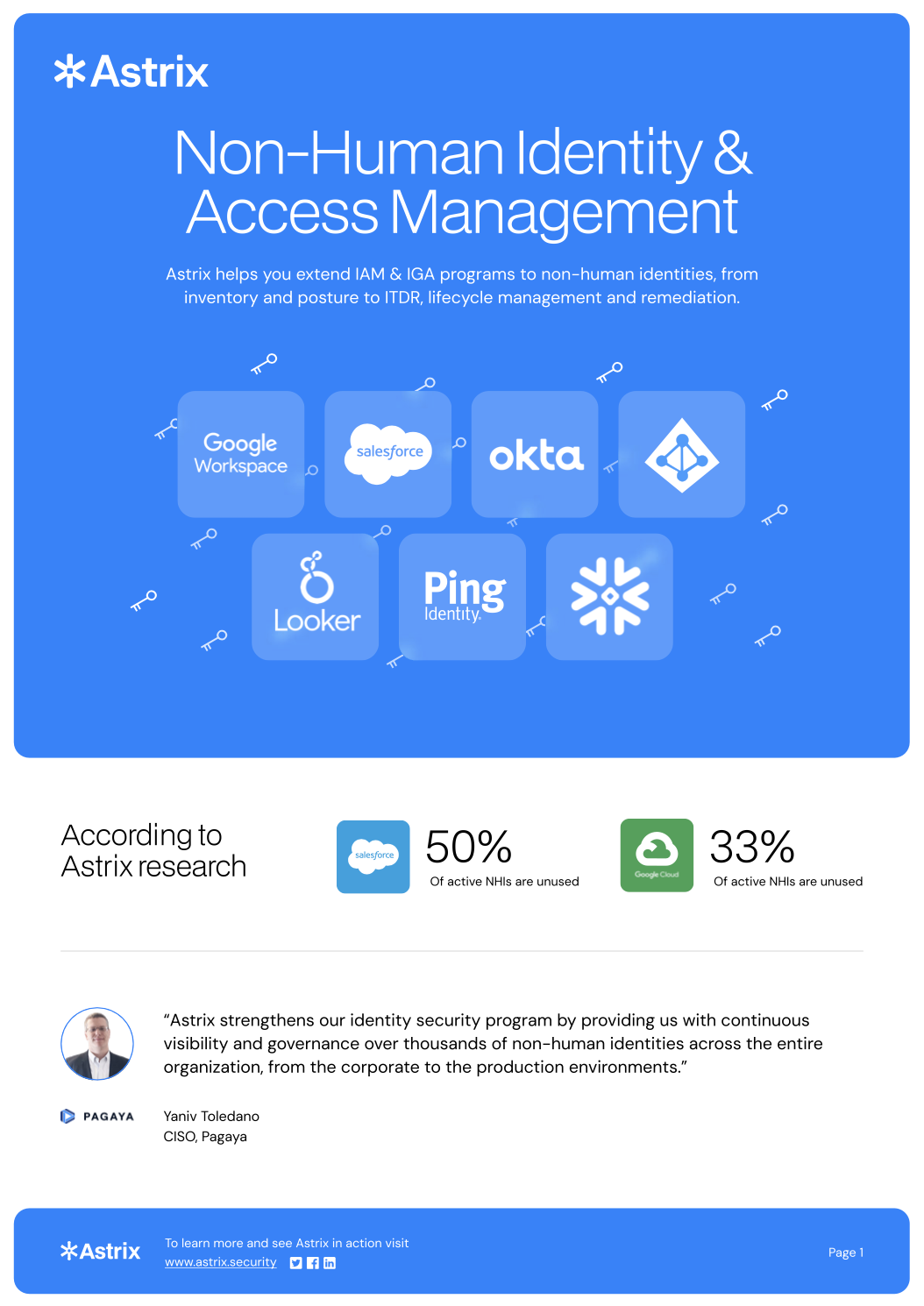
Astrix helps you extend IAM & IGA programs to non-human identities, from inventory and posture to ITDR, l…
The adoption of AI technology offers transformative opportunities but also significant risks, including data …
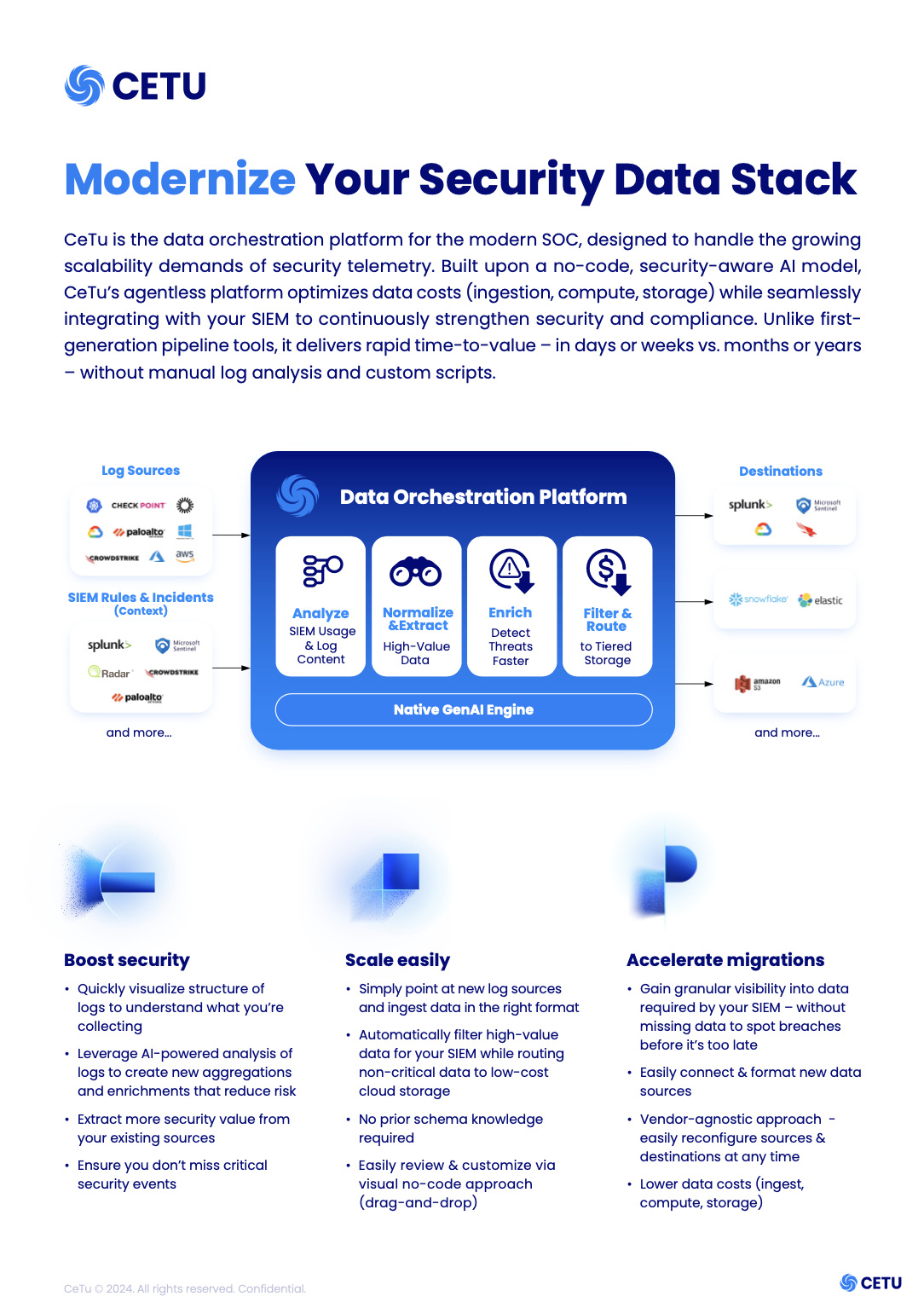
CeTu is the data orchestration platform for the modern SOC, designed to handle the growing scalability demand…
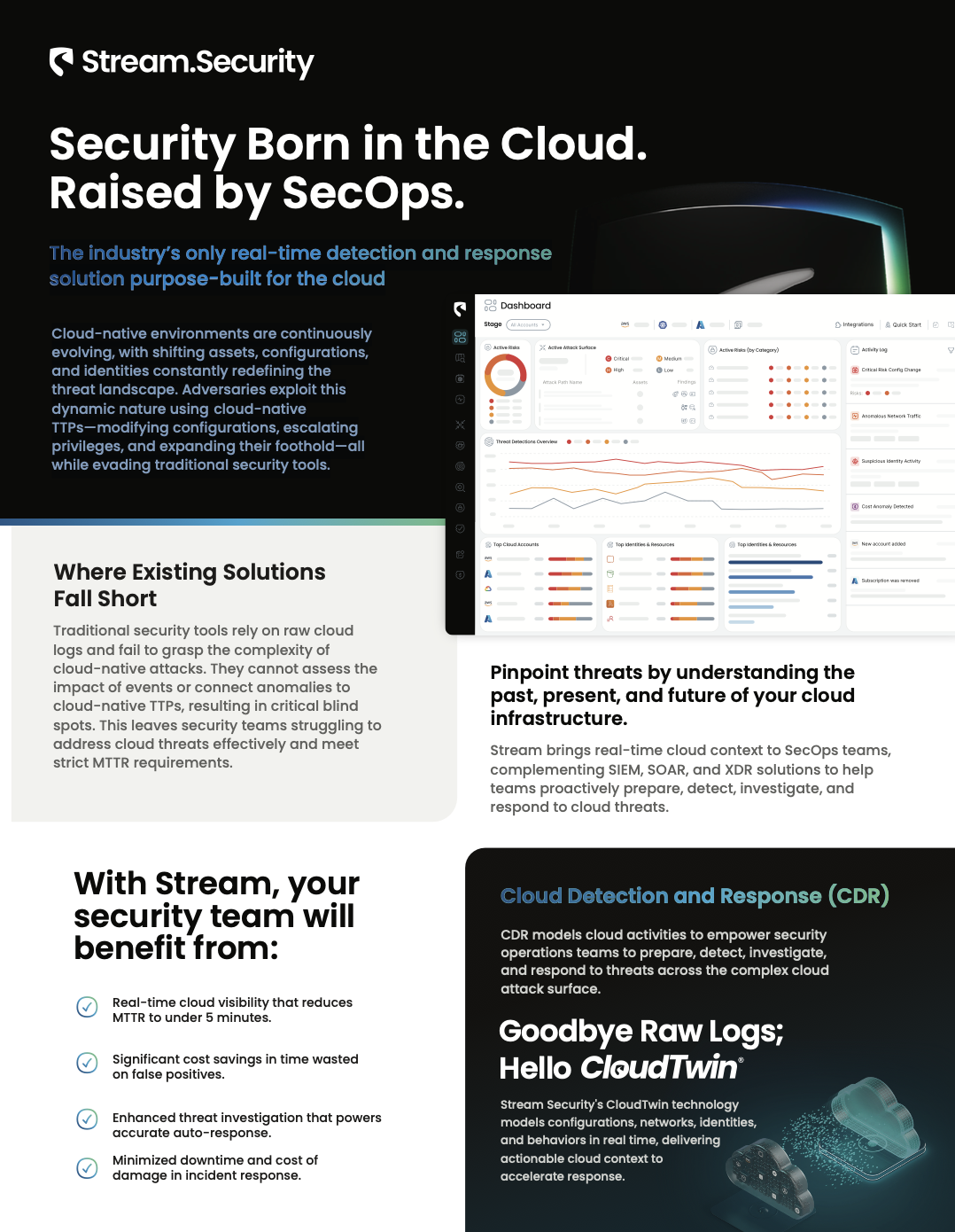
The industry’s only real-time detection and response solution purpose-built for the cloud Cloud-native enviro…
The rapid adoption of cloud technology has presented new security challenges that many teams were unprepared …
GenerativeAI (GenAI) has proliferated in the last few years. GenAI technology gives users the ability to quic…
Discover how the partnership of Presidio, Microsoft, and VMware helps customers seamlessly migrate and extend…
Integrating public and private cloud platforms poses unique obstacles that organizations must overcome to rea…
Experience the future of data-driven decision-making with your own Generative AI Business Assistant powered b…
Cribl, the Data Engine for IT and Security teams, uses the power of the cloud to create a globally distribute…
As the clear market leader, Cribl has more data than any other company about what IT and Security teams are d…
The most valuable perspective for defending against identity threats – a holistic identity encompasses the fu…
The 2024 Observability Forecast in Europe underscores how observability practices are evolving in response to…
Every day, William Hill publishes 5.1 million price changes—and everything is updated in real time. That’s 74…
Many organizations, particularly larger companies in the Global 2000, have more than a passing acquaintance w…
Digital business is the new reality for most enterprises. In IDC’s January 2024 Future Enterprise Resiliency …
Data is your organization’s most valuable asset. As “Dark AI” drives the exponential growth of sophisticated …
This report analyzes the current cloud storage security landscape, with a particular focus on the AWS S3 thre…
Amazon S3 is both cost effective and highly scalable, enabling quick and easy data sharing and storage across…
This is a sample assessment report for the types of AI security insights Wiz AI Security Posture Management (…
This guide focuses on GenAI to provide you with practical overview of best practices you can adopt to stat fo…
This brief outlines key best practices for enterprise-wide adoption of Copilot, focusing on achieving high us…
This white paper explores key ways executives can leverage Microsoft 365 Copilot to enhance their leadership …
This eBook explores practical use cases for Microsoft 365 Copilot in different functional areas of an organiz…
How effective preparation shortens the migration timeline, reduces the resource burden, and minimizes disrupt…
Klöckner Pentaplast drives sustainability using AWS IoT and Machine Learning Microservices
Blueprint of essential decisions to move JD Edwards EnterpriseOne to AWS
Key cybersecurity challenges facing healthcare organizations
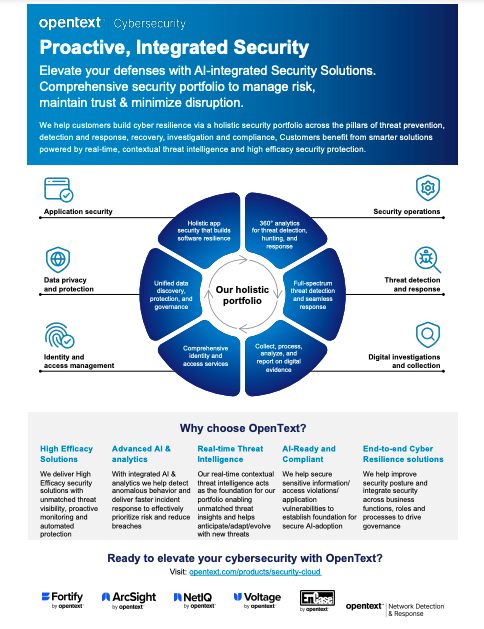
Elevate your defenses with AI-integrated Security Solutions. Comprehensive security portfolio to manage risk,…
Key cybersecurity challenges facing financial services organizations
Discover how multimedia service and support, automation, generative AI and natural language processing will s…
The Evolution of CX — CX Challenges
SASE unificado
This report describes the state of the malware and ransomware challenges today. The obstacles. The streng…
Security teams need reliable, definitive Darknet Data – regardless of the data exfiltration techniques us…
Harness the power of advanced AI by integrating Retrieval Augmented Generation (RAG) into your business ec…
Industry-specific benefits and use cases of AI 06 Financial services 07 Healthcare 08 Insurance 09 Lega…
It’s a challenging moment for those working in digital identity and security. Over half of organizations say …
Read on to learn: Your customers’ expectation of you The role customer identity plays in creating extraordin…
How Healthcare Business Can Thrive in a Tech-Driven Future
The consumerization of healthcare is driving a cascading force of differentiation from payers to providers to…
How to Prevent Breaches With Unified Identity and Access Management
Minimize your SaaS attack surface with advanced visibility and remediation to address configuration, identity…
This guide explains app development for SMBs. Apps are essential for business growth, with AI and machine lea…
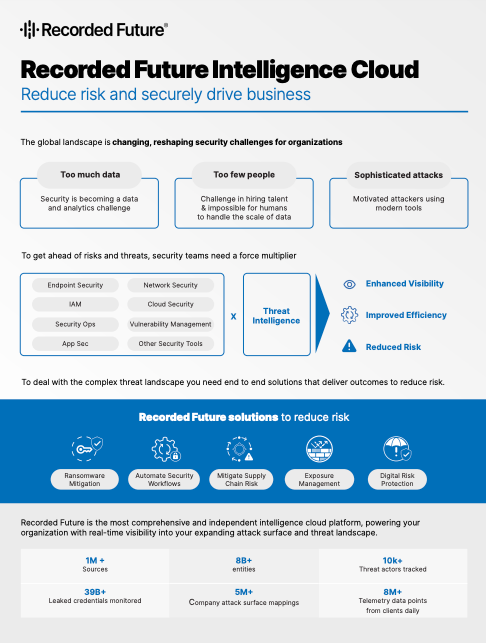
Reduce risk and securely drive business
In today’s ever-evolving threat landscape, organizations must adopt a proactive approach to stay one step ahe…
If you’re a cybersecurity leader looking for better network segmentation to defend your organization against …
Automated, Agentless Segmentation of Networks and Identities with Secure Remote Access
01 Thriving in a new technological environment 02 How generative AI can help the automotive industry 03 The o…
In today's interconnected world, the threat landscape is constantly evolving, demanding proactive measures fr…
As artificial intelligence (AI) technologies and particularly Generative AI (Gen AI) continue to evolve, so d…
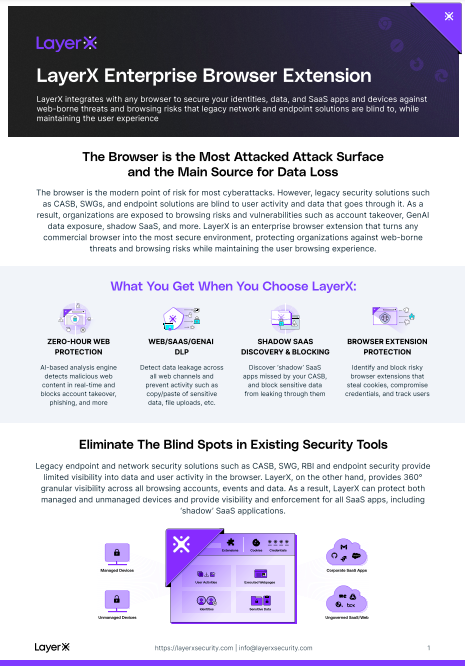
PROTECTION FROM WEB-BORNE THREATS STARTS WITH A BROWSER SECURITY PLATFORM
LayerX Enterprise Browser Extension The Browser Security Challenge
With new industry regulations, effective cybersecurity risk and operational management are more critical now …
Onyxia enables manufacturing leader to fully leverage Data Intelligence to strenghthen their security program…
LayerX integrates with any browser to secure your identities, data, and SaaS apps and devices against web-bor…
Ensure Reliable AI Performance by Prioritizing Data Quality
“How AI-ready is my organization?” This question has most likely crossed the minds of all forward-thinking en…
Get Data Ready for AI With Informatica’s AI-Powered Data Management Platform
Beckman Coulter Secures Data Management with Cohesity Backup as a Service.
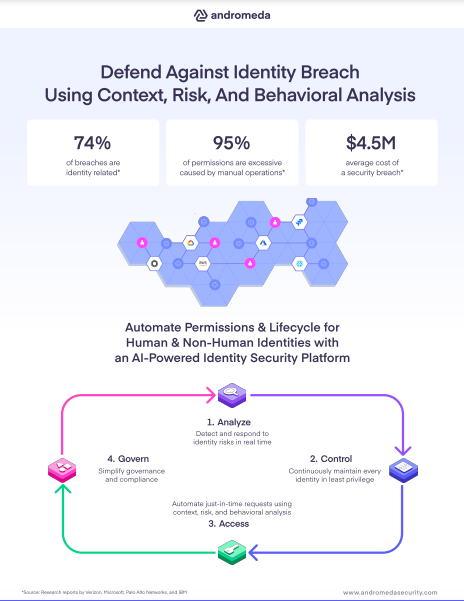
At Andromeda Security, our vision is to eliminate the negative impact of an identity breach by continuousl…
Defend against identity breach, using context, risk, and behavioral analysis.
The Power of Data Lies in Data Unification Building Your Data Strategy Bringing AI Into Your Data Program Man…
Unified Security and Log Analytics
Take supply chain resilience to the next level with Blue Yonder’s transformative cognitive planning solutions.
Dive into "Navigating the Future: The Essential Role of Multi-Faceted Automation in Modern Supply Chains" to …
Your AI security analyst to detect earlier, respond faster, and stay ahead of attacks.
Key Benefits • No upfront investment • Operational simplicity • Financial peace of mind
Protect. Detect. Recover with Cohesity and AWS
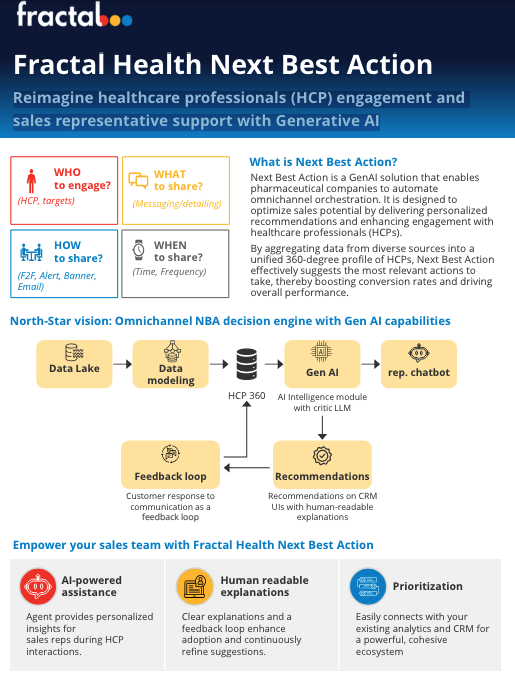
Streamline pharma decisions with AI-powered insights.
Improve pharma content efficiency with automated metadata creation.
Reimagine healthcare professionals (HCP) engagement and sales representative support with Generative AI.
Zero Trust Use Case 1: Increasing SaaS Visibility Zero Trust Use Case 2: Protecting Cloud Collaboration Zer…
Turn your data into dollars and make better business decisions. What is business observability?
Top takeaways from the largest, most comprehensive observability study.
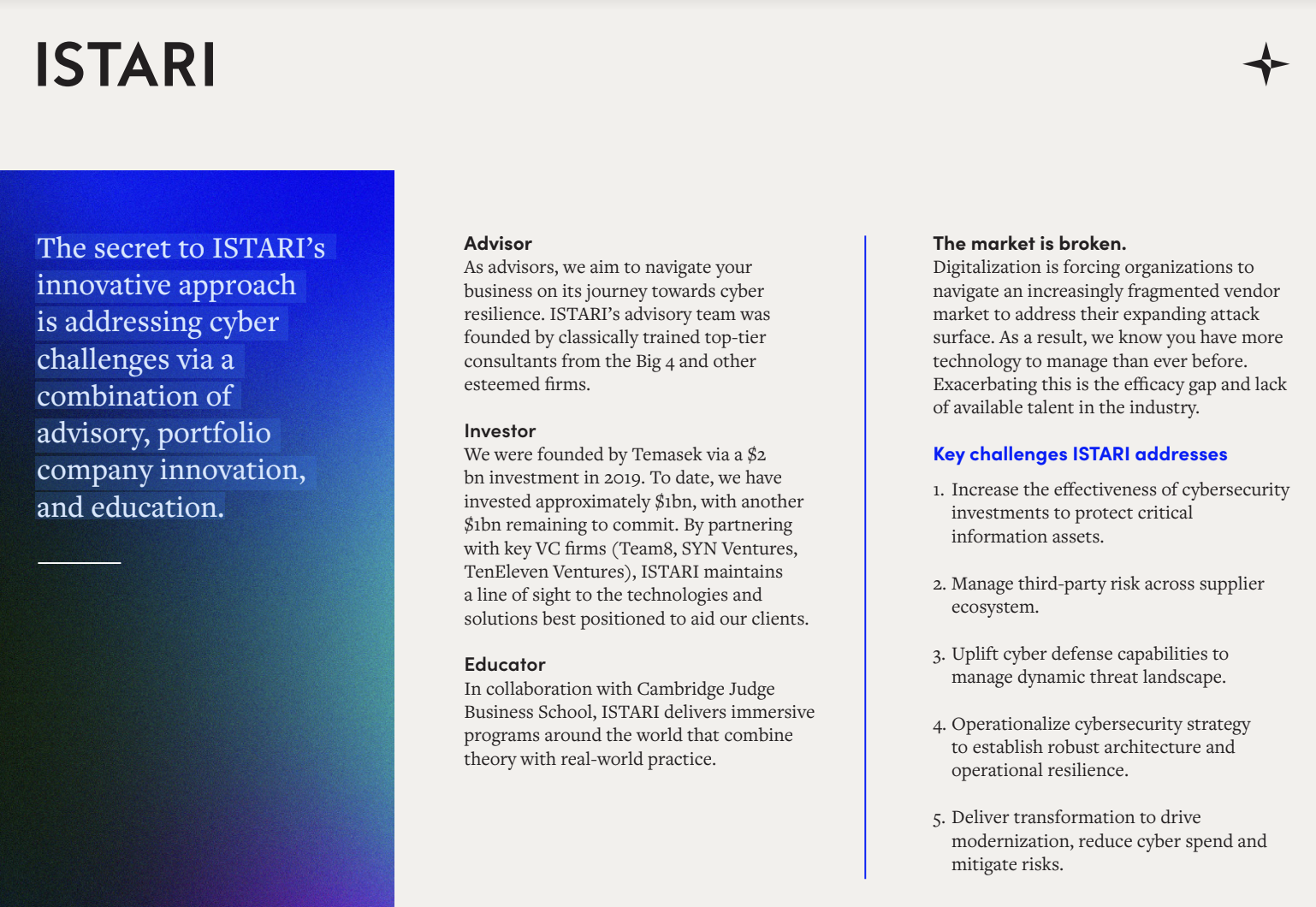
Executive education on cyber resilience.
The secret to ISTARI’s innovative approach is addressing cyber challenges via a combination of advisory, port…
With just a two week duration, AllCloud’s Generative AI and ML Assessment is designed to identify the ways AI…
Generative AI has the potential to revolutionize how companies of all sizes operate and serve their clients. …
With new industry regulations, effective cybersecurity risk and operational management are more critical now …
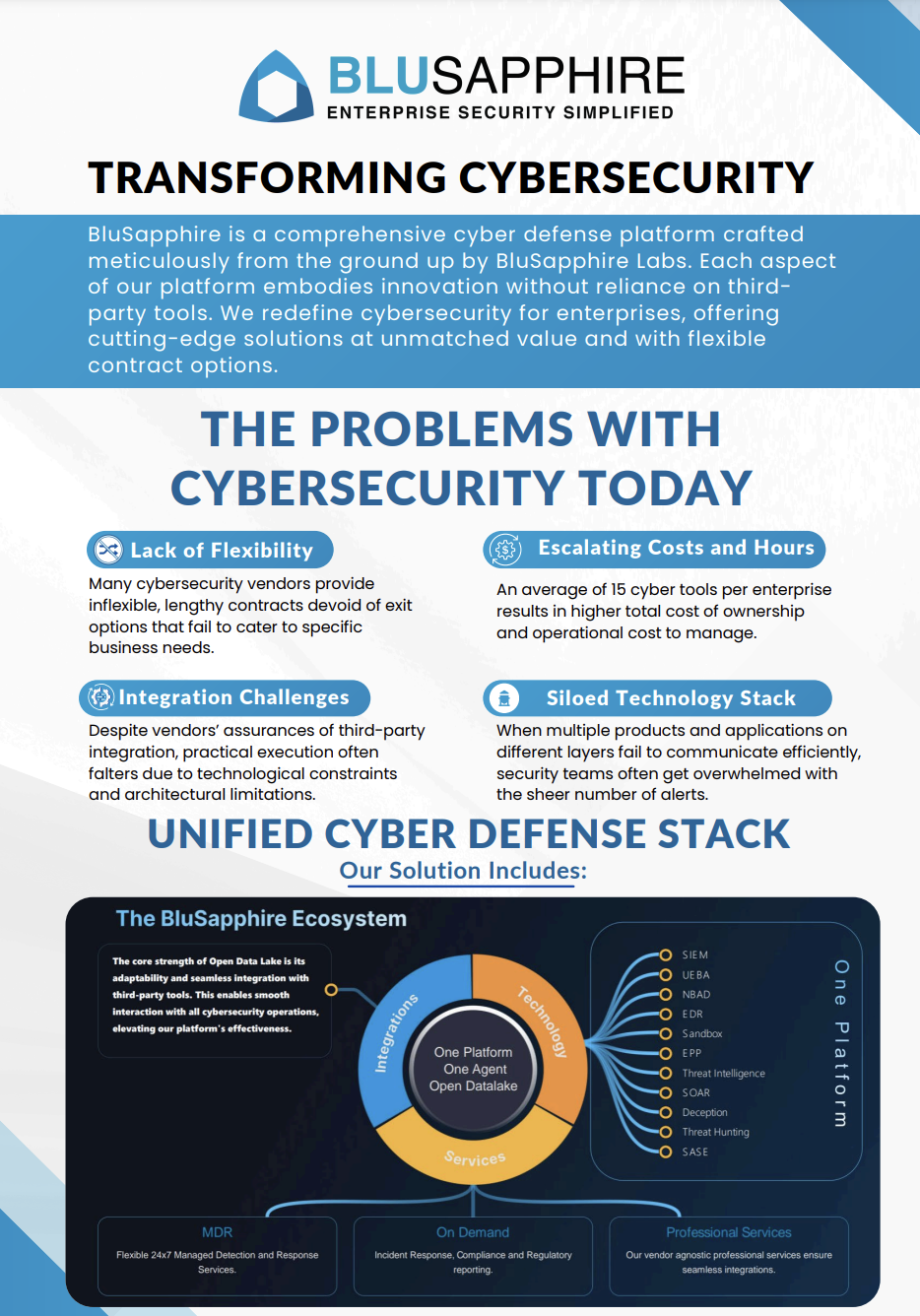
BluSapphire is a comprehensive cyber defense platform crafted meticulously from the ground up by BluSapphire …
BluSapphire's Revolutionary Security Data Lake solution represents a gamechanging leap towards cost-effective…
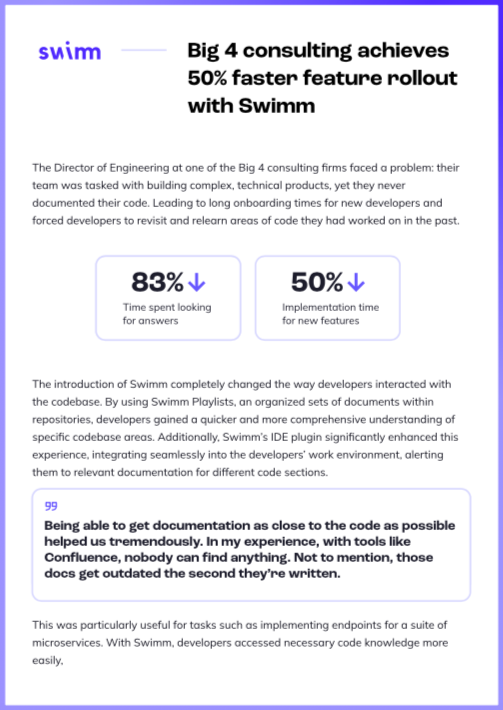
With almost all developers (92%) using or experimenting with AI coding tools, AI continues to transform …
Technical knowledge is siloed and lives in the mind of a few key devs, causing them to spend their time an…
The Director of Engineering at one of the Big 4 consulting firms faced a problem: their team was tasked wi…
We all know there’s work to be done to ensure all identities and perspectives are valued in the workplace,…
Azul Platform Prime is the world’s fastest, most scalable, and most efficient JVM. An enhanced version of…
Azul, provider of the Java platform for the modern cloud enterprise, is the only company 100% focused on …
Azul’s highly trained support engineers have extensive Java experience and deep knowledge of the JVM, mem…
Ad hoc professional services are designed to provide customers with a wide range of assistance for the var…
SentinelOne Singularity unifies and extends detection and response capability across multi- ple security …
The challenge of gaining visibility into all assets with sufficient context has hindered IT and security …
Chief Information Security Officers face an increasingly difficult set of responsibilities. They need cle…
By seamlessly integrating with over 750+ security and IT management technologies, Axonius Cybersecurity A…
In the landscape of ever-evolving security challenges, EliteOps introduces the Sprint program, an initiat…
At EliteOps, we stand out with our specialized, streamlined approach, breaking away from the generalized,…
Paycor is a human capital management company that provides HR and payroll technology to small and medium-…
Honeywell relied heavily on their channel partners for business growth and prospecting. They were looking…
New York Bariatric Group (NYBG) is an expert team of bariatric surgeons who provide surgical and non-surg…
Artificial Intelligence was created to make life easier. The technology completes tasks, quickly and effi…
This e-book provides a comparative look at how endpoint security solutions performed in the most recent AT…
As the demand for cyber insurance increases, so does the pricing and red tape. Discover how these challen…
In the realm of our highly connected world, the significance of cybersecurity has reached unparalleled hei…
senhasegura is a cybersecurity leader, specializing in Privileged Access Management (PAM) solutions that a…
Organizations often lack the capacity, resources, and expertise to properly identify and remediate supply…
Cybersecurity is more than detecting maliciousness. Frankly, the typical organization has a plethora of to…
ThreatLocker® is a Zero Trust endpoint protection platform that provides enterprise-level cybersecurity to or…
Supercharge Your Anti-Phishing Defense with PhishER Plus.
In this ebook, you’ll find relevant information to help you with the following questions: What should you be…
Old-school security awareness training doesn’t hack it anymore. Today, your employees are frequently exposed …
Report SummaryDevices running ThreatLocker® vs. not running ThreatLocker® 206 out of 42,000. To capture a com…
Routing data to the right tools and destinations gives you the flexibility to optimize your observability…
This solution guide provides a holistic view of the Cribl solution, and how it enables open observability…
All data has value, but not all at once. Today’s excess data may be exactly whatyour company needs later t…
The promise of quantum computing is tantalizing. Once quantum machines become sufficiently powerful, tasks…
In a world where everything is connected and nothing is trusted, public key infra- structure (PKI) is the …
PlayPlay helps Heifer International create more videos to engage its communities. Both for Internal Co…
Everywhere you look, there are videos competing for attention–on social media feeds, web browsers, on giant s…
In today's digital landscape, the role of a Chief Information Security Officer (CISO) is becoming more and …
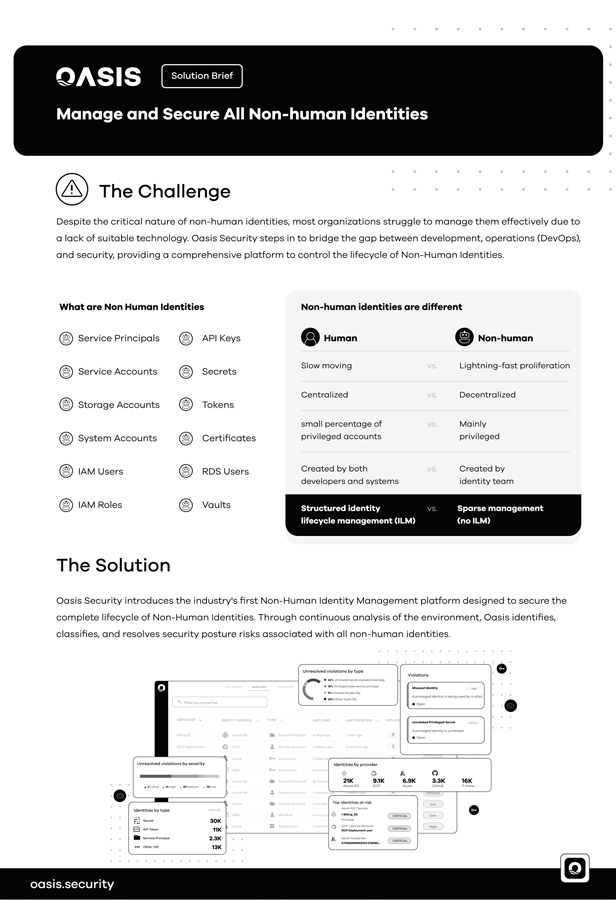
Despite the critical nature of non-human identities, most organizations struggle to manage them effectively d…
Application Allowlisting denies all applications from running except those that are explicitly allowed. This …
Revisit the Basics to Learn How A Different Approach Can Prevent More Attacks
Microsoft Windows Servers have been the fundamental basis of small and large business networks since the ear…
Many organizations utilize security testing (a.k.a penetration testing) to validate the security posture of t…
Ransomware is blackmail: an extortion proposition where bad actors seek to monetize hijacked data from an org…
Traditional vulnerability management approaches can no longer keep up with today’s dynamically changing busin…
Public key infrastructure (PKI) isn’t anything new. It’s been around for decades. Beginning as the trust engi…
The need for Crypto-Agility: How to know when your cyber security is past its expiration date.
Ready or not, the quantum era is coming. Protect your digital assets, applications, and infrastructure with c…
When your IT infrastructure resides in an enterprise data center, at the network edge, and in remote and bran…
Today’s digital economy has fundamentally transformed the pace and expectations of IT operations teams charge…
Operating and managing complex IT environments, particularly hybrid clouds, becomes time-consuming and costly…
How cloud-based technologies are impacting enterprise infrastructure, operations, and strategies.
Tracking customer experience (CX) metrics is essential for organizations aiming to understand their audiences…
In today’s experience economy, brands win or lose by their ability to deliver contextual and compelling perso…
With the rise of digital transformation and the growing number of channels that marketing teams support, tech…
Most security testing programs, particularly penetration testing, are compliance driven and performed once or…
Accelerate the FedRAMP process from 18 months to 3* and reduce preparation time by 50 - 60% with RegScale’s u…
Wiz partnered with RegScale to unite its new best-in-class cloud security posture management system with RegS…
What you need to know to prepare and recover from a ransomware attack.
The vendor landscape for security awareness training (SAT) is as diverse as it is innovative. This market has…
Picture this: you're scrolling through social media and you come across a video of a celebrity doing somethin…
Alarm bells are sounding off in College Park, Maryland.According to a recent study, researchers doubt it will…
The cloud landscape has grown significantly over the past decade due to which many organizations are making t…
How a Multinational Pharmaceutical Company Uses Cyera to Improve Data Security and Compliance
How Cyera Helped a Mortgage Lender Secure and Manage Sensitive Data
Harden your data security posture across your hybrid cloud. Cyera puts data first and focuses on rapid time t…
Each day, Cybersixgill collects approximately 10 million intelligence items from the deep, dark, and clear we…
Cybersixgill’s intelligence feed reduces incident response times by 75%
How to Protect Critical Assets Through Systematic, Proactive Threat Intelligence.
Headquartered in New York, NY, Goldman Sachs is a leading global banking, securities, and investment manageme…
According to Bain & Company, 2023 M&A activity will be on par with or exceed the level of activity in…
Forward Networks industry-leading verification platform, Forward Enterprise, analyzes and verifies network be…
Protecting your data in AWS is your responsibility. Cohesity Data Protect delivered as a service running on A…
Data is at the center of every organization. From home, remote, and branch office locations to on-premises da…
Organizations worldwide are facing continued economic uncertainty that challenges expected outcomes. As predi…
Transforming your organization’s business and culture through IT leadership
How do you know if your company is truly innovative?
Innovation as the driving force for sustainability Sustainability is a societal initiative that aims for huma…
Drive better visibility across SecOps by taking control of your data.
Gaining control over observability and security data, like metrics, logs, and traces, is criticalfor today’s …
Metrics, events, logs, and traces contain critical information about your customers andoperating environment.
The increasing threat and impact of ransomware is not going to subside until we develop better strategies for…
Relentlessly Future Focused, so you can be too.
Do you really know how many applications employee have connected to your organization's Google Workspace acco…
Do you really know how many third-party applications have access to your GifHub repository?
Many security and IT teams are concerned about a substantial security gap in their data warehouses such as GC…
How CYE helps you understand the true cost of cyber incidents and remediation so you can optimize security bu…
How to strengthen your security posture and optimize security investments by assessing and prioritizing cyber…
Assess, quantify, and mitigate your cyber risk.
Recipes for a Secure Cloud
Find Your Path to Successful Cloud Expansion
Security Awareness Training (SAT) has long been a central approach for companies seeking to educate their emp…
According to a 2022 survey by Osterman Research, the majority of cybersecurity leaders do not have an effe…
Sika is a specialty chemicals company with a leading position in the development and production of systems an…
We take responsibility for every project from beginning to end, providing full visibility throughoutwith our …
Kubernetes is the de facto standard for container orchestration. While good practice, image scanning alone is…
Server/VM Workload Detection & Response, part of the Singularity Cloud family, defends workloads running …
Digital transformation is more than a buzzword. It’s the process of evolving from rigid, legacy on-premises p…
Despite some time in the limelight as an overused buzzword, zero trust, for many organizations, has emerged a…
A multinational investment and financial services company, providing services to customers across more than 5…
Digital transformation has reshaped the world, improving the way businesses interact with customers, workers,…
Cyberattacks are inevitable—and nation-state and ransomware attackers are savvier than ever in “living off th…
Despite the deployment of PAM and MFA solutions, Illusive discovers privileged identity risks on 1 in every 6…
Illusive discovers and mitigates privileged identity risk policy violations that are exploited in all ransomw…
lllusive continuously discovers and automatically mitigates privileged identity risks and policy violations t…
Illuminating identity risks that leave every organization vulnerable to attack
Today’s businesses handle vast amounts of sensitive information, such as personally identifiable information …
With the rapid expansion of digital operations, protecting sensitive data has become a top priority for organ…